Onboard your Mobile Engineering Team into your Security Challenges
Onboarding a team on Mobile App security requires many ingredients to make sure your iOS and Android mobile applications are not an open door to hackers.
It leads your team to take into account the specifics of mobile environments: acquire specific knowledge and make sure that processes are in place to implement security protections and avoid any vulnerabilities.
And this is inevitably a challenge, since the development is managed by many people, and many SDK 3rd party libraries are part of the mobile app.
It only takes 3 steps:
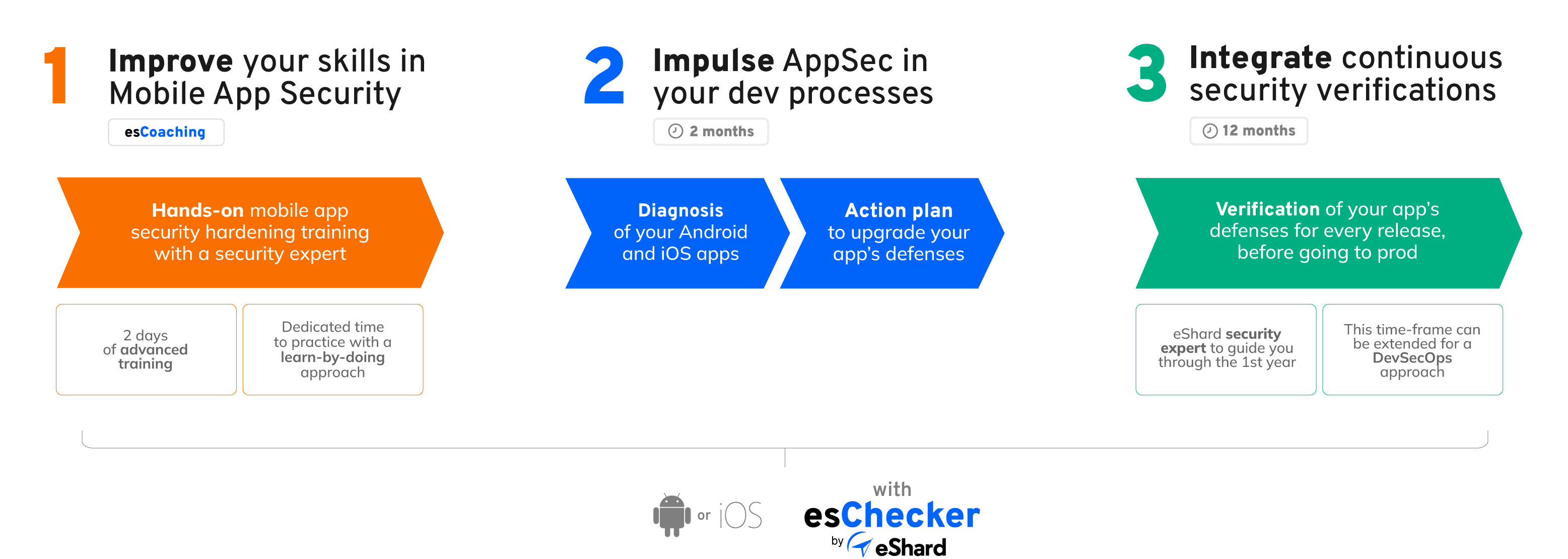
We designed this specific offering for any leader willing to empower their engineering team and impulse a sustainable initiative for gaining control of the in-house mobile app security.
This bundle offer combines a skill development part, with
Your needs,
Our solutions.
Mobile application security and related threats may be unfamiliar to team members. It becomes necessary to empower them and create confidence to improve the process and the code. How to provide them with the right support to implement defensive codes?
Build confidence in mobile app security within the team.
Through a learn-by-doing approach, upskill mobile engineering teams on secure mobile app development practices for defensive code and awareness on related risks.
Digitalization led users to shift to mobile apps. Now that the traffic has moved from web apps to mobile apps, security processes and verifications must shift accordingly.
This requires setting up a specific culture of mobile app security, one that keeps in mind a flowing development cycle with many releases a year.
Shared understanding of the current situation.
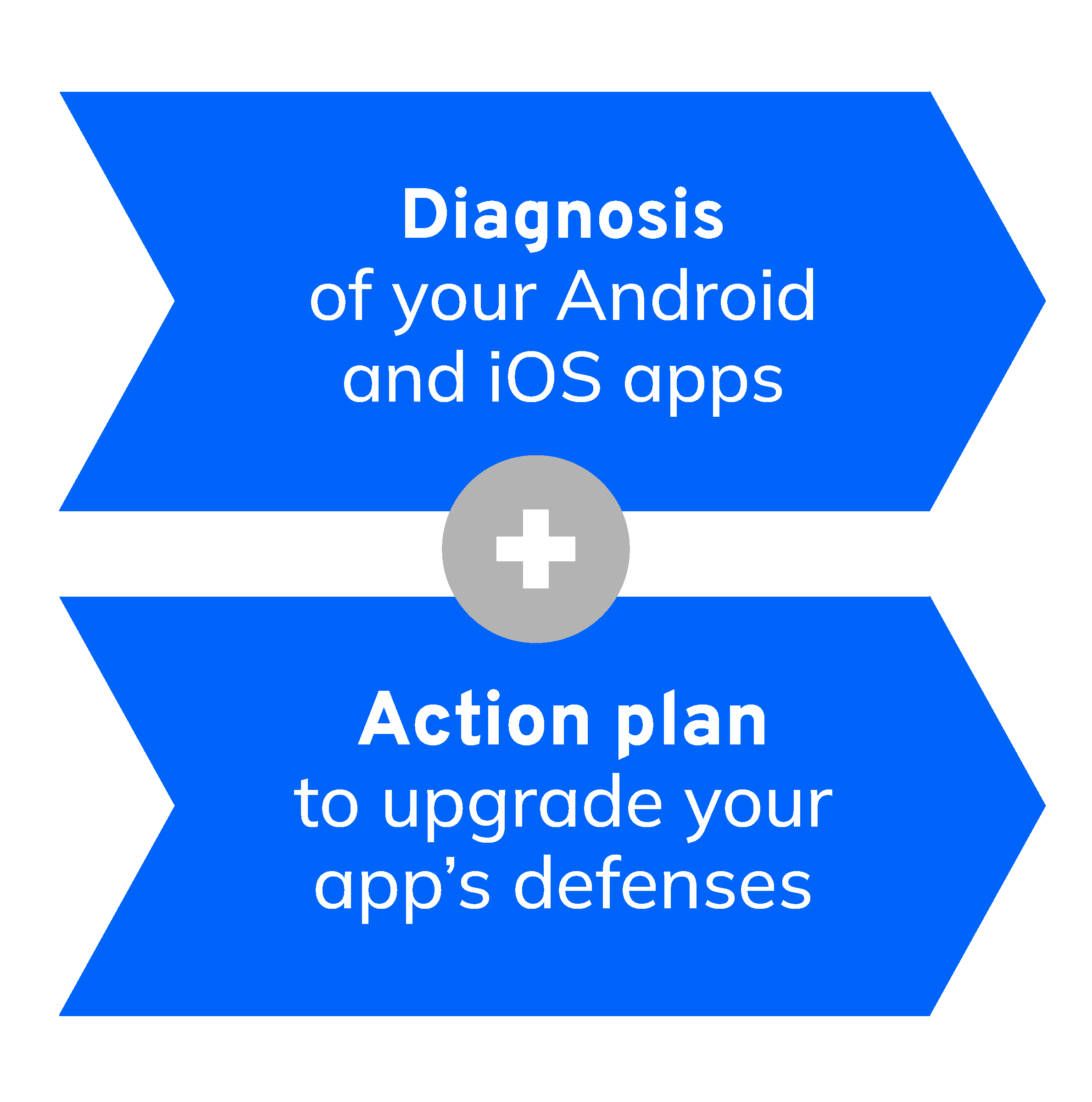
Impulse a diagnosis of the current application security posture (Android or iOS). This should be the starting point to initiate a continuous improvement. A shared collaboration between the team and eShard experts creates confidence.
Action plan to improve the mobile app security.
Once the diagnosis is set, the action plan shared with eShard experts gives clear steps for integrating mobile app security within the development process.
You are accountable for the whole app. It integrates many 3rd party SDKs which makes it difficult to ensure control.
How can you make sure there is a consistent security policy enforced for all releases?
Integrate security verifications in the development process.
Testing is performed at the binary level: it integrates all codes, including 3rd party SDKs. Enforce non-regression testing with a minimal impact on the development cycle.
This is why we created
Mobile AppSec Onboarding


This is the first step towards impulsing mobile application defensive development. How are attacks against apps are carried out? How can weaknesses be efficiently identified? What countermeasures to implement and how?
By answering these questions, our esCoaching module on Mobile Application Defensive Development (Android or iOS) will provide your team with the necessary knowledge and hands-on practice to start building confidence in AppSec.

Impulsing the mobile application security in your development processess requires having a clear starting point.
Our experts will work collaboratively with your teams to share a diagnosis of your current iOS or Android mobile applications' protections followed by an action plan. This process will be based on your binary files and it will take into account the outcome of the dynamic and static analysis made by esChecker.
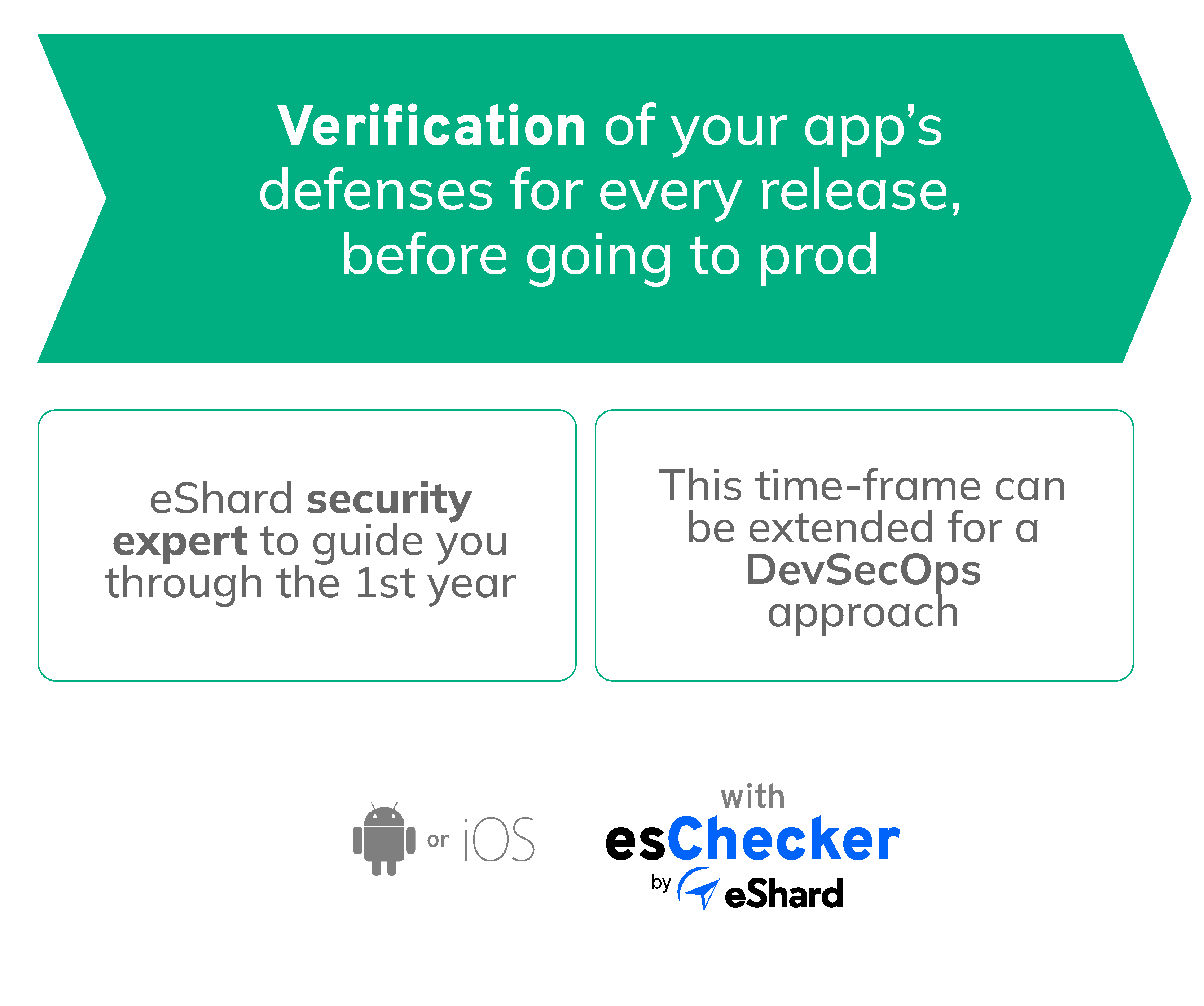

Integrating continuous security verifications aims at making sure that each of your mobile application releases has a controlled quality in terms of security and defensive measures.
In short, our MAST tool esChecker is integrated into your development processes to perform security verifications prior to putting the applications in production. With this routine in place, your team can identify vulnerabilities and adopt defensive measures for each release, therefore avoiding security regressions.
Opt for a deeper integration within your development cycle by considering an integration of esChecker into your CI/CD pipeline for a DevSecOps approach.

